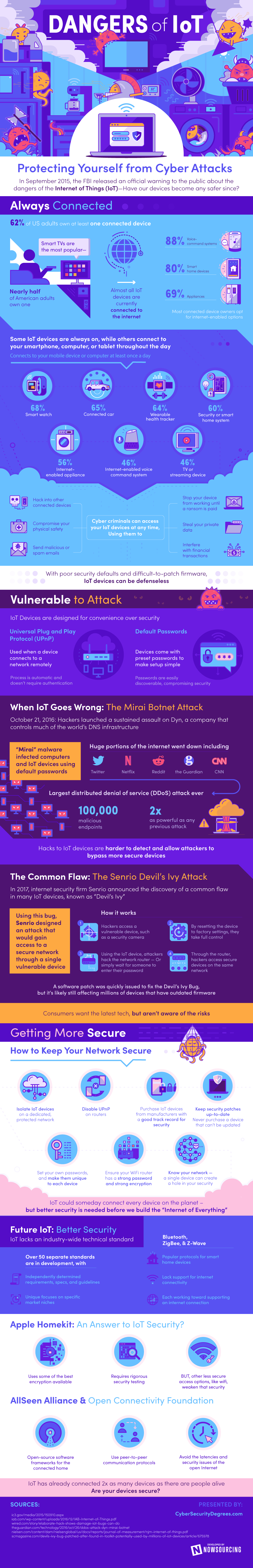
Dangers of IoT: Protecting Yourself from Cyber Attacks
In September 2015, the FBI released an official warning to the public about the dangers of the Internet of Things (IoT) ㄧ Have our devices become any safer since?
Always Connected
62% of US adults own at least one connected device
Smart TVs are the most popular ㄧ Nearly half of American adults own one
Nearly all IoT devices are currently connected to the internet
Among connected device owners, most opt for Internet-enabled options
Voice-command systems: 88%
Smart home devices: 80%
Appliances: 69%
Some IoT devices are always on, while others connect to your smartphone, computer, or tablet throughout the day
Device connects to smartphone, computer, or tablet, at least once a day
Smart watch: 68%
Connected car: 65%
Wearable health tracker: 64%
Internet-enabled home control devices/systems: 60%
Internet-enabled appliances: 56%
Internet-enabled voice command systems: 46%
Smart TV or streaming device: 46%
Cyber criminals can access your IoT devices at any time ― Using them to
Hack into other connected devices
Send malicious or spam emails
Steal your private data
Compromise your physical safety
Stop your device from working until a ransom is paid
Interfere with financial transactions
With poor security defaults and difficult-to-patch firmware, IoT devices are vulnerable to attack
Vulnerable to Attack
IoT Devices are designed for convenience over security
Universal Plug and Play Protocol (UPnP)
Used when a device connects to a network remotely
Process is automatic and doesn’t require authentication
Default Passwords
Devices come with preset passwords to make setup simple
Passwords are easily discoverable, compromising security
When IoT Goes Wrong: The Mirai Botnet Attack
October 21, 2016: Hackers launched a sustained assault on Dyn, a company that controls much of the world’s DNS infrastructure
“Mirai” malware infected computers and IoT devices using default passwords
Huge portions of the internet went down, including Twitter, Netflix, Reddit, the Guardian, and CNN
Largest distributed denial of service (DDoS) attack ever
100,000 malicious endpoints
2x as powerful as any previous attack
Hacks to IoT devices are harder to detect and allow attackers to bypass more secure devices
Common Flaw: The Senrio Devil’s Ivy Attack
In 2017, internet security firm Senrio announced the discovery of a common flaw in many IoT devices, known as “Devil’s Ivy”
Using this bug, Senrio designed an attack that would gain access to a secure network through a single vulnerable device
How it works:
Hackers access a vulnerable device, such as a security camera
By resetting the device to factory settings, they take full control
Using the IoT device, attackers hack the network router — or simply wait for someone to enter their password
Through the router, hackers access secure devices on the same network
A software patch was quickly issued to fix the Devil’s Ivy Bug, but it’s likely still affecting millions of devices due to the difficulty of updating the firmware on these devices
Consumers want the latest tech, but aren’t aware of the risks
Getting More Secure
How to Keep Your Network Secure
Isolate IoT devices on a dedicated, protected network
Disable UPnP on routers
Purchase IoT devices from manufacturers with a good track record for security
Keep security patches up-to-date ― Never purchase a device that can’t be updated
Set your own passwords, and make them unique to each device
Ensure your WiFi router has a strong password and strong encryption
Know your network — a single device can create a hole in your security
IoT could someday connect every device on the planet – but better security is needed before we build the “Internet of Everything”
Future IoT: Better Security
IoT lacks an industry-wide technical standard
Over 50 separate standards are in development, with
Independently determined requirements, specs, and guidelines
Unique focus on specific market niches
Bluetooth, ZigBee, & Z-Wave
Popular protocols for smart home devices
Lack support for internet connectivity
Each working toward supporting an internet connection
Apple’s HomeKit: An Answer to IoT Security?
Uses some of the best encryption available
Requires rigorous security testing
BUT, Other less secure access options, like wifi, weaken that security
AllSeen Alliance & Open Connectivity Foundation
Open-source software frameworks for the connected home
Use peer-to-peer communication protocols
Avoid the latencies and security issues of the open Internet
IoT has already connected 2x as many devices as there are people alive ― Are your devices secure?
Sources:
https://www.ic3.gov/media/2015/150910.aspx
https://www.iab.com/wp-content/uploads/2016/12/IAB-Internet-of-Things.pdf
https://www.theguardian.com/technology/2016/oct/26/ddos-attack-dyn-mirai-botnet
https://www.wired.com/story/elaborate-hack-shows-damage-iot-bugs-can-do/
https://www.scmagazine.com/devils-ivy-bug-patched-after-found-in-toolkit-potentially-used-by-millions-of-iot-devices/article/675978/
https://www.nielsen.com/content/dam/nielsenglobal/us/docs/reports/journal-of-measurement/njm-internet-of-things.pdf